



Not only since the revelations of Edward Snowden has it been known that all data that we outsource to the cloud, both in our digital private lives and in our working environment, is under certain circumstances a highly insecure matter. This is why end-to-end encryption, or client-side encryption, is so important for data protection.
End-to-end encryption means that messages are encrypted at the sender and only decrypted at the intended recipient. At no point in between are they available in unencrypted form. Client-side encryption is therefore the prerequisite for true end-to-end encryption.
Even if you are of the opinion that your data is safely stored and only you have access to it, there is usually an institution that could have access to your data: Your cloud provider. With the latter, there's no need for absurd conspiracy theories. Secret services and investigating authorities can, for example, demand a court order from the cloud provider to hand over your files. Or if - as has already happened several times - the security mechanisms of a cloud provider are hacked, your data is freely accessible and unencrypted on the network. All these possibilities must be countered with modern encryption techniques.
However, file encryption only makes sense if it is continuously effective from the beginning to the end of a transmission path. Both the files themselves and the transfer into and out of the cloud must be encrypted.
All of the above requirements are met by encryption technologies based on end-to-end encryption. Multiple encryption instances with public keys and private keys and the corresponding certificates are used. The respective certificates document the authenticity and the legitimation of the authorized partners. Files that are to be outsourced to the cloud in order to share them with other authorized persons are encrypted directly at the user's location and sent to the cloud server via an additionally encrypted transmission path. From there the data can be accessed by authorized persons - of course, this transfer to the file recipient is also encrypted. The files are only decrypted again at the recipient's end. You see: At no point within the transmission path via the encrypted cloud are the file contents visible. The only thing that the central instance of such a technology "sees" on an administrative level are the respective access permissions (individuals and groups of people), the actual contents cannot be decrypted there either.
This method is called end-to-end encryption, including client-side encryption. For this to work, everyone who wants to participate in the data exchange must generate an asymmetric key pair and make the public key available on the exchange platform.
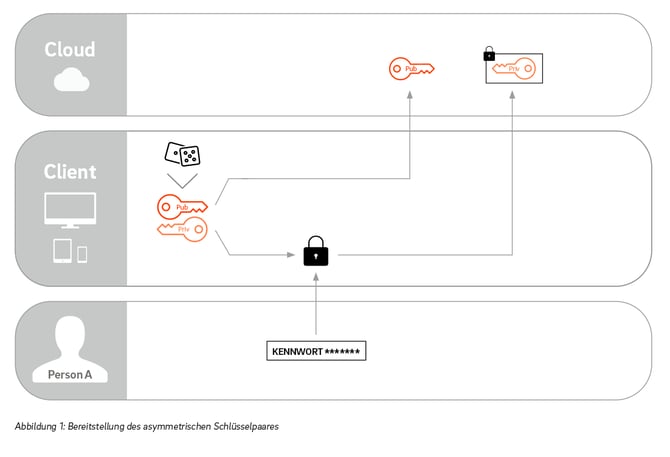
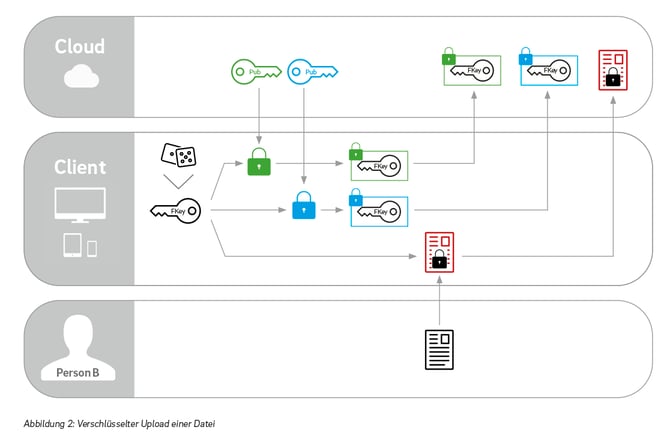
A user who wants to upload a file for a group of people first gets the public keys of the recipients. He then generates a symmetric key for himself with which he encodes the file. He then creates a copy of this symmetric key for each recipient and encrypts it with the respective public keys. Finally, he transfers the encrypted copies of the symmetric key together with the encrypted file to the server and stores them there.
If another user wants to download the file, he gets it in the encrypted form together with the copy of the symmetric key that is encrypted for him. He can decrypt the latter using his private key and now has the symmetric key with which he can decode the file.
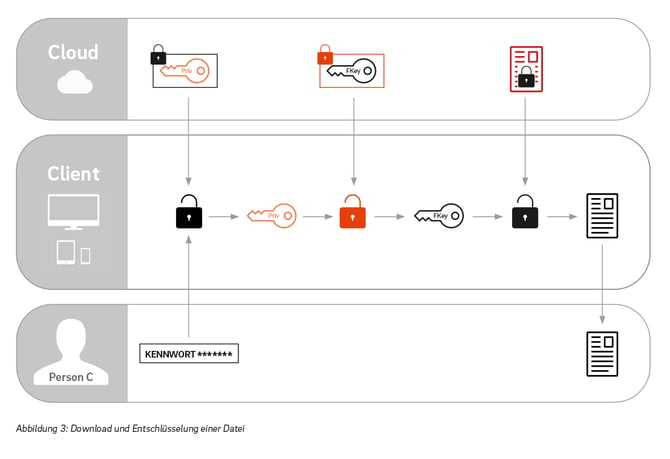
So the user first encrypts his files with his own key and transfers them to the server or the cloud. The key that encodes his data never leaves his client or computer in plain text.Therefore, there is no possibility to decrypt the files on the server itself. This means that no third party, not even the cloud operator, has access to the stored data.
Since with client-side encryption, all files are already encrypted on the user's computer, the cloud provider and attackers who have gained access to the server system are denied the opportunity to access the files. This means that data cannot be handed over by the provider at the request of an authority.
Internal offenders can also be better prevented with client-side encryption, since with this variant no one except the sender and authorized recipients have access to the decrypted data. In this way, the circle of people who should have access to certain data can be minimized. Likewise, the administrator can also be deprived of access to sensitive data, such as wage costs.
The General Data Protection Regulation (GDPR) tightens the security requirements for companies. Client-side encryption is best suited to meet these requirements.
Requirement |
Explanation |
Solution |
|
Pseudonymisation: Personal data should no longer be able to be attributed to a specific data subject without additional information, provided that this additional information is kept separately and is subject to technical and organisational measures which ensure that the personal data is not attributed to an identified or identifiable natural person. |
Encryption is a form of pseudonymisation. The key stands for the additional information. If the key is kept together with the data, encrypted data can be made publicly accessible, e.g. in the event of a phishing attack. Pseudonymisation is then no longer possible. |
Client-side encryption: On the server itself there is no possibility to decrypt the files, e.g. in case of a phishing attack, because only encrypted key material is stored there. |
|
Appropriate technical and organisational measures to secure personal data: The measures shall take into account the state of the art, the implementation costs as well as the type, scope, circumstances and purpose of the processing. In addition to these criteria, the different probabilities of occurrence and the severity of the risk to the rights and freedoms of the data subjects must also be taken into account. Accordingly, the level of security measures taken should be adapted. Encryption is explicitly mentioned as such a measure in the non-exhaustive catalogue of Art. 32 (1) EU-GDPR. |
In order to ensure adequate protection, personal data should be encrypted. However, not all types of encryption provide the same level of protection. For maximum security, encryption keys should be controlled by the user. No one else should have access to them during the encryption and decryption process. |
Client-side encryption: The key that encodes the data never leaves the user's computer in plain text. |
|
Loss of data: You must report a data breach if it poses a risk to the data subject. According to Art. 4 No. 12 GDPR, a violation of personal data exists if personal data have been lost or have been destroyed, altered or disclosed without authorisation. |
In the event of a data protection breach, the responsible person must report the breach to the competent supervisory authority without delay and, if possible, within 72 hours of becoming aware of the breach. Unless the breach is unlikely to create a risk to the protection of personal data. |
Client-side encryption: If client-side encryption is used, it is impossible to decrypt the files in case of an attack on the server, because the key is held by the owner. Therefore, hacks on servers are not considered as data mishaps and the notification rules of the GDPR do not apply. This means that you save the cost of data failure notifications and possible fines, maintain your reputation and protect the privacy of your employees and customers. |
|
Sanctions: The supervisory authorities shall ensure that the fines provided for in the article for infringements of the GDPR are effective, proportionate and dissuasive in each individual case. |
Fines are imposed according to the circumstances of the individual case. In deciding on the imposition and the amount thereof, account shall be taken in each individual case of the measures taken. |
Client-side encryption: Since all files are encrypted on the user's end device, only unreadable data can be known. These are not considered personal data or data mishaps. Fines are therefore avoided. |
With the following five rules, you can easily assess for yourself whether a cloud encryption concept really offers you security:
A modern end-to-end encryption works platform-independent and cross-platform on all end devices. Being able to encrypt files easily should be a matter of course for you.
While client-side encryption was previously relatively difficult to implement and manage, it is now already integrated into modern solutions. This makes it particularly easy for you as a user to use, because you no longer have to deal with the installation of certificates or keys. With DRACOON, for example, you simply choose your personal decryption and encryption password - you start immediately and the encryption runs reliably in the background.

© 2023 DRACOON GmbH
Made in Germany
Phone. +49 (941) 7 83 85-0